
Table 4.1 from An Efficient Security Aware Routing Protocol for Mobile Ad Hoc Networks | Semantic Scholar

Secure Multipath Routing Protocols in Wireless Sensor Networks: A Security Survey Analysis | Semantic Scholar

Trust-based secure routing and message delivery protocol for signal processing attacks in IoT applications | The Journal of Supercomputing

Securing WBAODV Routing Protocol in MANETs: Towards Efficient and Secure Routing Protocol: Elmasry, Wisam: 9783659268793: Amazon.com: Books

Hierarchical energy efficient secure routing protocol for optimal route selection in wireless body area networks - ScienceDirect
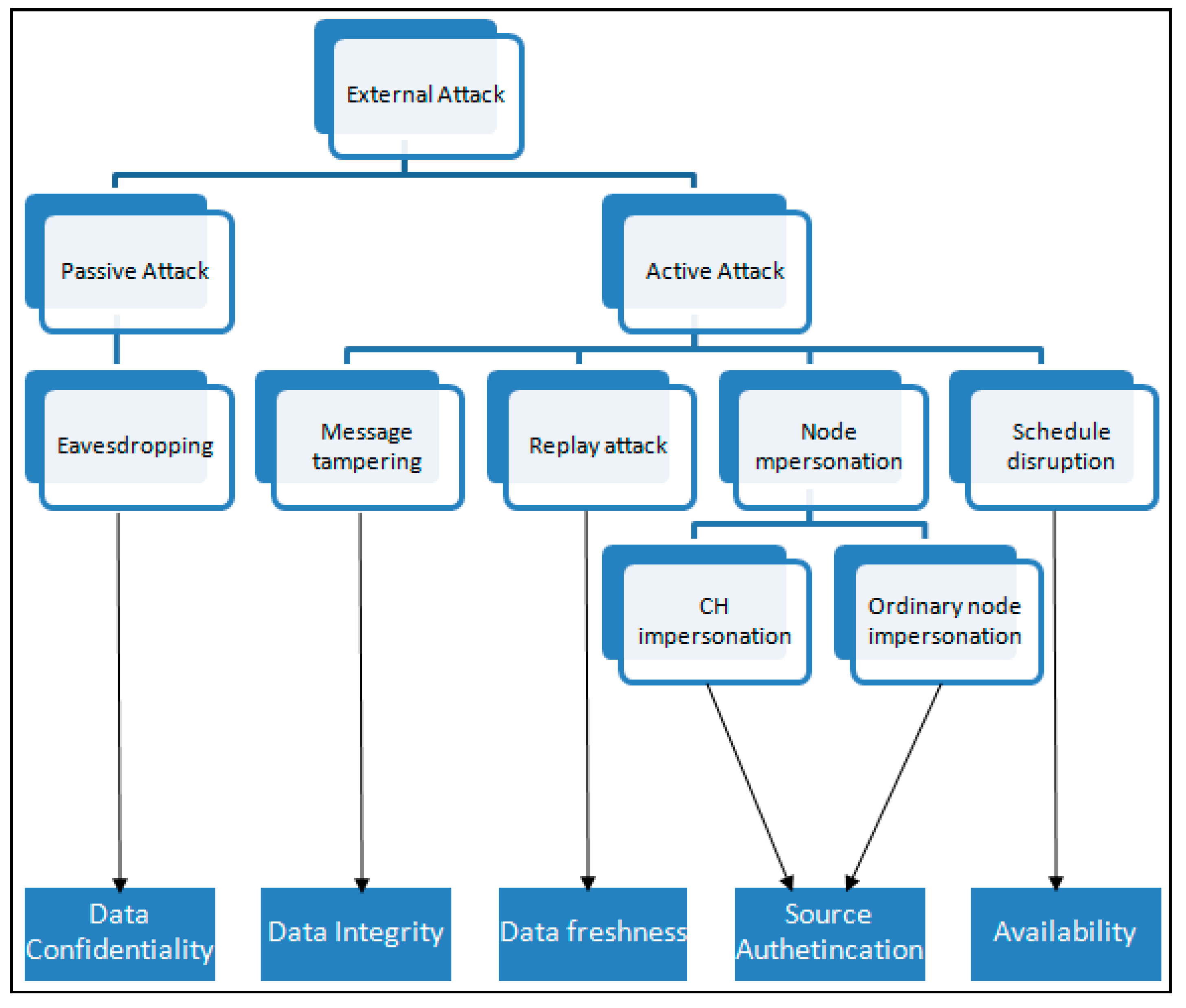
Sensors | Free Full-Text | A Secure Routing Protocol for Wireless Sensor Networks Considering Secure Data Aggregation
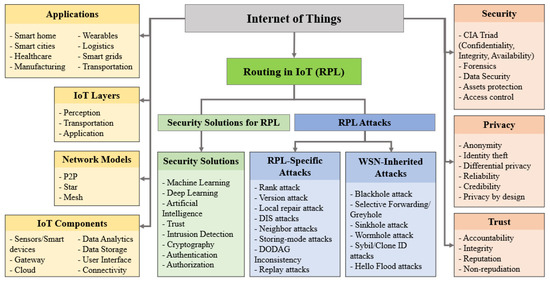
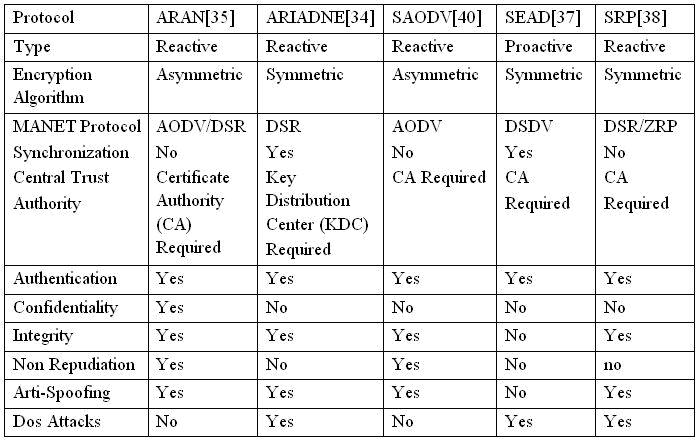






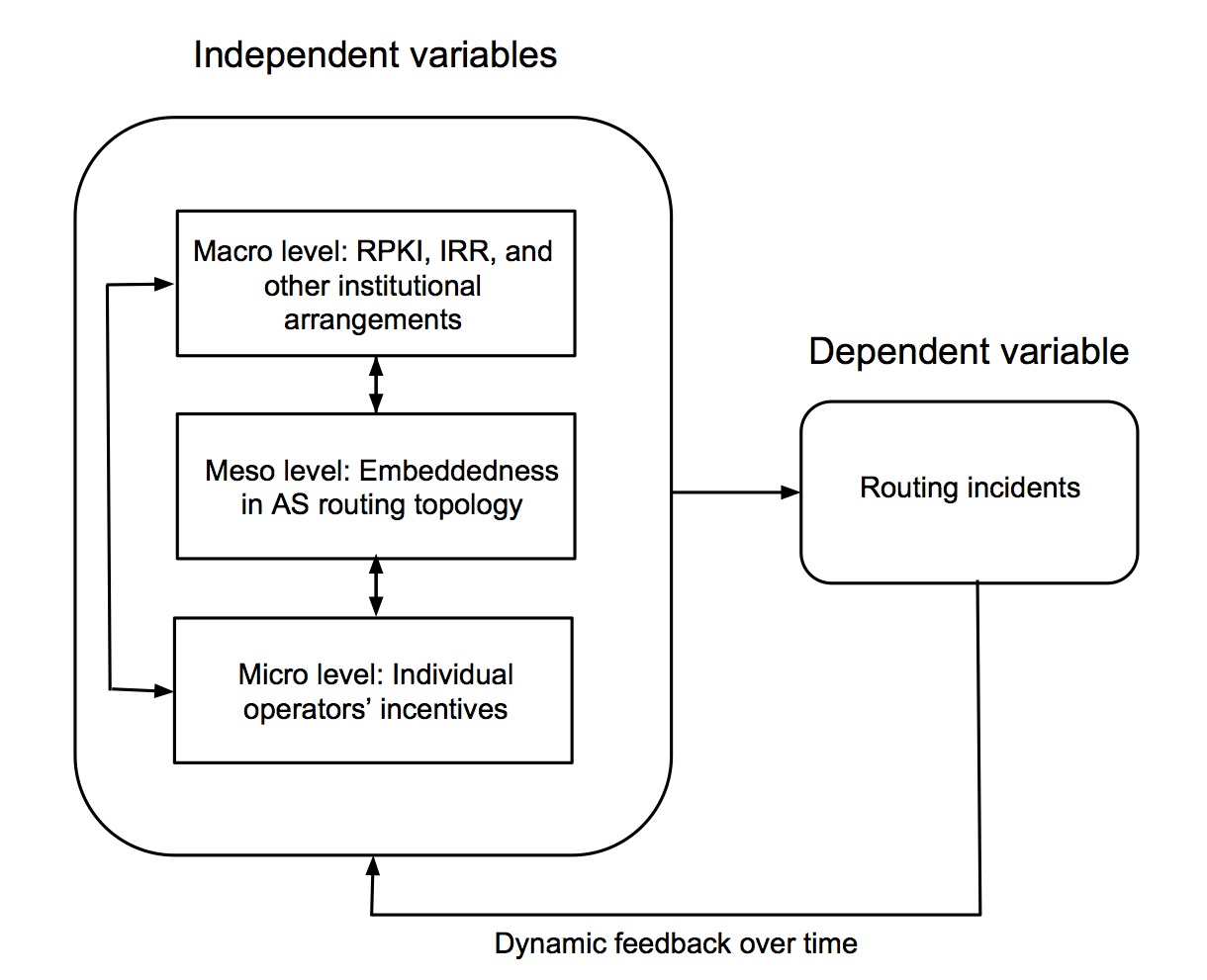
![PDF] A Security-Aware Routing Protocol for Wireless Ad Hoc Networks | Semantic Scholar PDF] A Security-Aware Routing Protocol for Wireless Ad Hoc Networks | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/4194e46bfc559e52a5389a3dd61ea9c40c90553b/1-Figure1-1.png)






