
Data Mining: How to Protect Patient Privacy and Security When Using Data - Electronic Health Reporter

Privacy and Security Issues in Data Mining and Machine Learning: International ECML/PKDD Workshop, PSDML 2010, Barcelona, Spain, September 24, 2010. Revised Selected Papers | SpringerLink

Emerging Technologies in Data Mining and Information Security: Proceedings of IEMIS 2018, Volume 1 | SpringerLink







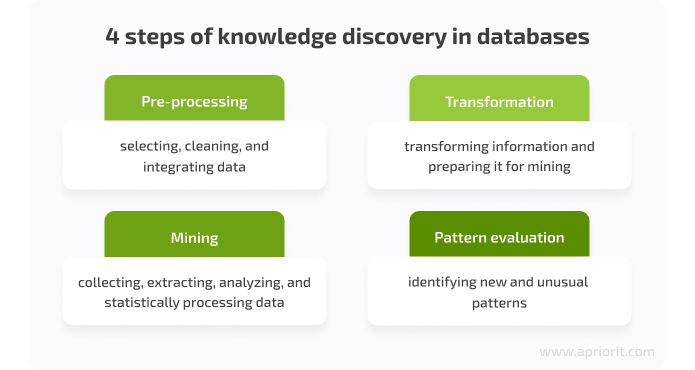
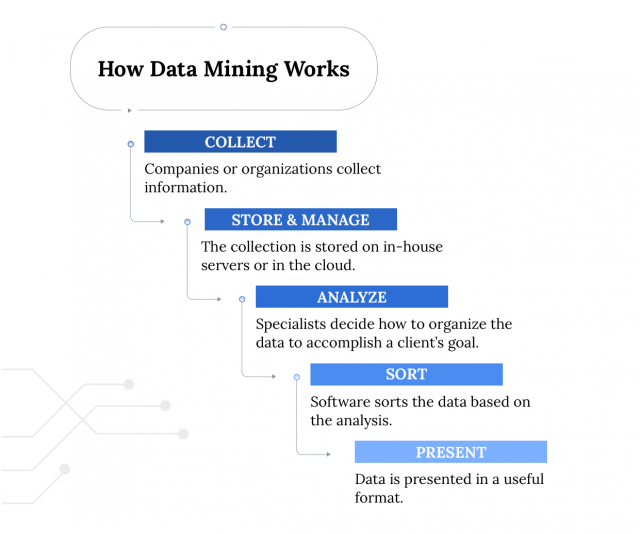
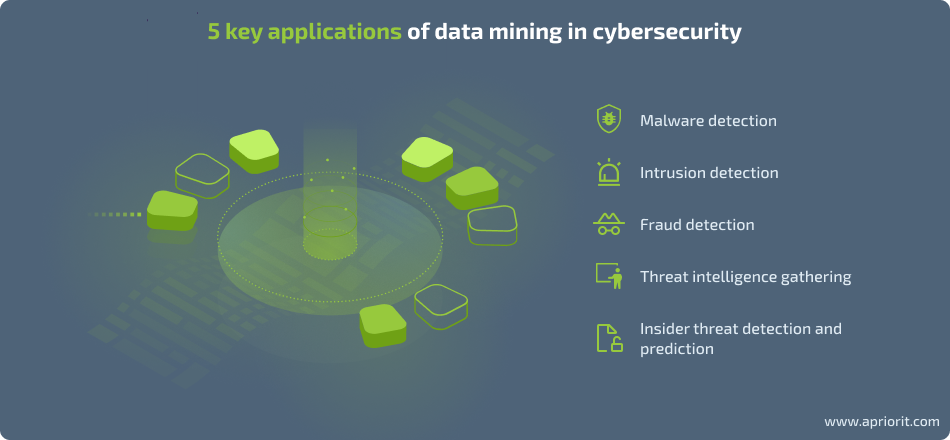




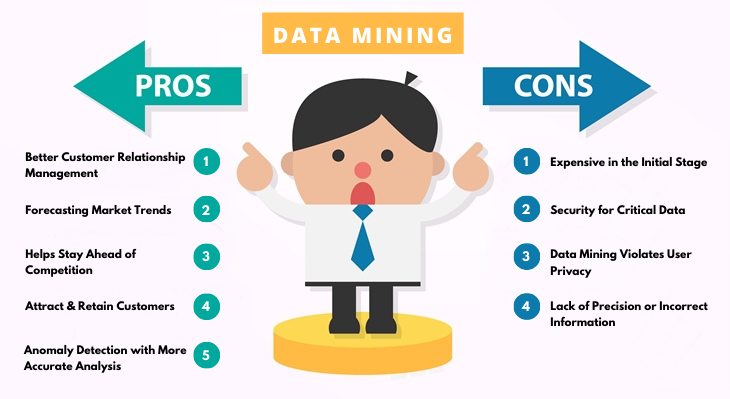




![PDF] Exploiting the Data Mining Methodology for Cyber Security | Semantic Scholar PDF] Exploiting the Data Mining Methodology for Cyber Security | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/605c1ec7a2af2b10b81831ab0a49f29a94d47ca7/3-Table1-1.png)
